The 2024 holiday season revealed a complex and evolving threat landscape for Distributed Denial-of-Service (DDoS) attacks. This year’s trends included advanced tactics such as an increase in DDoS-for-hire operations, the assembly of massive DDoS botnets by script kiddies, politically motivated attack campaigns, and the bypass of CDN (Content Delivery Network) protections among other evolving threats.
The 2024 holiday season attack landscape in Azure
During the holiday season, we noted a shift in attack patterns from last year, highlighting how malicious actors continuously refine their tactics to bypass DDoS protection.
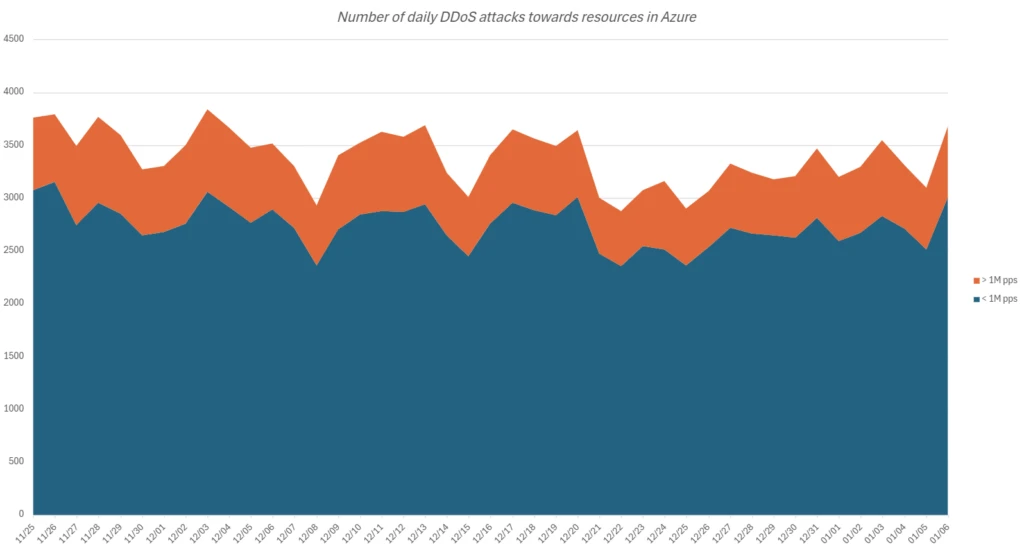
Daily attack volume
Azure’s security infrastructure mitigates up to 3,800 attacks daily. Large-scale attacks over one million packets per second (pps) make up about 81% of these, similar to last year’s analysis. Highly volumetric attacks exceeding 10M pps are rare, at just 0.2% of all attacks, reflecting attackers’ aim to minimize resources and avoid detection.
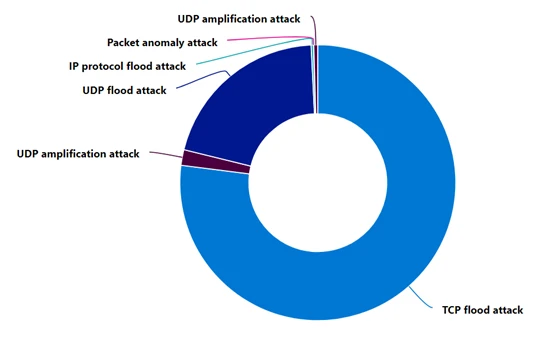
Attack protocols
The 2024 holiday season saw a predominant use of TCP-based attacks (Transport Control Protocol), targeting various web applications and resources, accounting for 77% of the attacks. This is in contrast to last year when UDP-based attacks (User Datagram Protocol) accounted for nearly 80% of the attacks on gaming and other resources. The main TCP attack vectors this year were TCP SYN (Synchronize) and ACK (Acknowledge) floods.
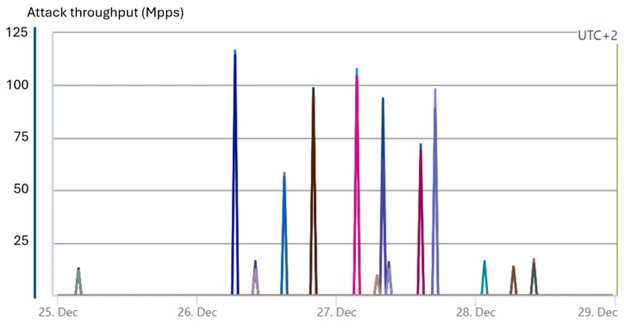
Azure blocks massive typhon attack
A staggering attack on gaming resources reached 100-125 million pps in multiple waves. This attack, whose signatures link to Typhon botnet, was fully mitigated by Azure’s defenses.
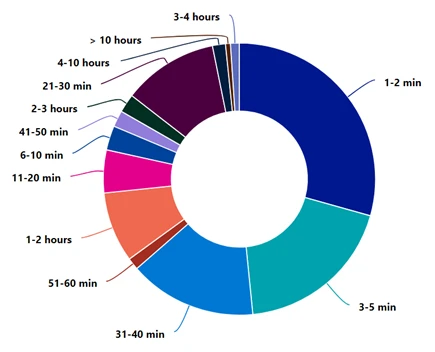
Attacks duration
This holiday season again we witnessed the same adversaries’ tactics of trying to bypass DDoS mitigation strategies by launching burst or short-lived attacks. 49% of all attacks lasted up to 5 minutes, whereas 83% of attacks lasted less than 40 minutes. It is insightful to understand that any DDoS mitigation countermeasure we implement to protect our application should kick in effective mitigation as soon as possible.
Political motives and DDoS-for-hire surge
This holiday season, Azure’s attack trends reflect global patterns. Politically motivated attacks, driven by geopolitical tensions, persist. DDoS threats remain a significant concern as new actors use available tools to cause disruption.
The rise of DDoS-for-hire services, often referred to as stressers and booters, has gained significant popularity among attackers. These platforms, which are readily accessible on cybercriminal forums, have democratized the capability to launch robust DDoS attacks, making them attainable for less sophisticated criminals at minimal costs. In recent years, there has been an increase in both the availability and utilization of these services. During this holiday season, international law enforcement agencies conducted operations such as Operation PowerOFF last December, resulting in the arrest of three individuals and the shutdown of 27 domains associated with DDoS-for-hire platforms. Despite these efforts, DDoS stressers continue to thrive, offering a variety of attack methods and power, and are likely to persist in their prevalence.
Preparing for 2025
The 2024 holiday season has emphasized the ongoing threat of DDoS attacks. Organizations must enhance their cybersecurity strategies to counter these evolving threats in the new year. Strengthening defenses and staying vigilant to new tactics is crucial in 2025. Azure’s resilience against advanced DDoS threats highlights the importance of robust security measures for protecting digital assets and ensuring business continuity.
Identifying exposure points
Start by pinpointing which of your applications are exposed to the public internet. Evaluating the potential risks and vulnerabilities of these applications is crucial to understanding where you may be most susceptible to attacks.
Recognizing normal operations
Familiarize yourself with the normal behavior of your applications. Azure provides monitoring services and best practices to help you gain insights into the health of your applications and diagnose issues effectively.
Simulating attack scenarios
Regularly running attack simulations is an effective way to test your services’ responses to potential DDoS attacks. During testing, validate that your services or applications continue to function as expected and that there’s no disruption to the user experience. Identify gaps from both a technology and process standpoint and incorporate them into your DDoS response strategy.
Ensuring robust protection
With the high risk of DDoS attacks, it’s essential to have a DDoS protection service like Azure DDoS Protection. This service provides always-on traffic monitoring, automatic attack mitigation upon detection, adaptive real-time tuning, and full visibility of DDoS attacks with real-time telemetry, monitoring, and alerts.
Implementing layered security
For comprehensive protection, set up a multi-layered defense by deploying Azure DDoS Protection with Azure Web Application Firewall (WAF). Azure DDoS Protection secures the network layer (Layer 3 and 4), while Azure WAF safeguards the application layer (Layer 7). This combination ensures protection against various types of DDoS attacks.
Configuring alerts
Azure DDoS Protection can identify and mitigate attacks without user intervention. Configuring alerts for active mitigations can keep you informed about the status of protected public IP resources.
Formulating a response plan
Establish a DDoS response team with clearly defined roles and responsibilities. This team should be adept at identifying, mitigating, and monitoring an attack, as well as coordinating with internal stakeholders and customers. Use simulation testing to identify any gaps in your response strategy, ensuring your team is prepared for various attack scenarios.
Seeking expert assistance
In the event of an attack, reaching out to technical professionals is vital. Azure DDoS Protection customers have access to the DDoS Rapid Response (DRR) team for assistance during and after attacks. Following an attack, continue monitoring resources and conduct a retrospective analysis. Apply learnings to improve your DDoS response strategy, ensuring better preparedness for future incidents.
Call to action
The 2024 holiday season highlighted the evolving threat landscape of DDoS attacks, with a significant increase in DDoS-for-hire operations, massive botnets, and politically motivated campaigns. These threats emphasize the need for robust DDoS protection and a DDoS response plan. Azure supports organizations to stay ahead of these threats. Customers should enable multi-layer protection by deploying Azure DDoS Protection with Azure Web Application Firewall (WAF). Additionally, customers should enable telemetry and alerting capabilities to monitor and respond to active mitigations effectively.
The post Navigating the 2024 holiday season: Insights into Azure’s DDoS defense appeared first on Microsoft Azure Blog.
Leave a Reply