It has been three years since SAP Sapphire last occurred in person, and I was thrilled to meet with our customers and partners again this week. As SAP Sapphire comes to a close, I am taking a moment to reflect on how the world has changed since the pandemic. Many organizations were not prepared for […]
Manage Red Hat workloads seamlessly on Azure
Every year, Red Hat Summit features inspirational and actionable content, industry-shaping news, and innovative practices from customers and partners. From hybrid cloud, containers, and cloud-native app platforms to management, automation, and more, speakers from around the world, across industries, and sectors join to share how they're using open tools to build better solutions for themselves […]
Manage Red Hat workloads seamlessly on Azure
Every year, Red Hat Summit features inspirational and actionable content, industry-shaping news, and innovative practices from customers and partners. From hybrid cloud, containers, and cloud-native app platforms to management, automation, and more, speakers from around the world, across industries, and sectors join to share how they're using open tools to build better solutions for themselves […]
Accelerating innovation in the diabetic foot market with Azure Health Data Services
This blog post has been co-authored by Sharlene Jerome, Manager of Marketing and Communications, Sensoria Health This blog is part of a series in collaboration with our partners and customers leveraging the newly announced Azure Health Data Services. Azure Health Data Services, a platform as a service (PaaS) offering designed exclusively to support Protected Health […]
Join us and the developer community to celebrate Azure Static Web Apps
Join us to celebrate the one-year anniversary of Azure Static Web Apps! Come connect with others in the developer community and increase your Azure Static Web Apps skills in a fun, collaborative way. It's hard to believe that it was just under a year ago that we announced the general availability of Azure Static Web […]
Streamline Azure workloads with ExpressRoute BGP community support
In today’s globalized world, customers have started to maintain and expand their presence in the cloud across different geographic regions. With these increased deployments across Azure regions comes the increased complexity of customers’ hybrid networks. Establishing connectivity is no longer as simple as exchanging IP addresses between one pair of Azure regions and on-premises locations. […]
Customize your secure VM session experience with native client support on Azure Bastion
This blog post has been co-authored by Isabelle Morris, Program Manager, Azure Networking As organizations move their mission-critical workloads to the cloud, connecting to virtual machines (VMs) directly over the public internet is becoming more of a security risk. The more public IP addresses a customer has attached to VMs in their virtual network, the […]
Customize your secure VM session experience with native client support on Azure Bastion
This blog post has been co-authored by Isabelle Morris, Program Manager, Azure Networking As organizations move their mission-critical workloads to the cloud, connecting to virtual machines (VMs) directly over the public internet is becoming more of a security risk. The more public IP addresses a customer has attached to VMs in their virtual network, the […]
Intelligent application protection from edge to cloud with Azure Web Application Firewall
Threat intelligence at scale! Changes to how we work and operate our businesses have driven every company to now be a digital company. This acceleration in digital transformation has also led to a rise in security risks. Cyberattacks are becoming more common and advanced with growing attack surfaces due to the proliferation of mobile and […]
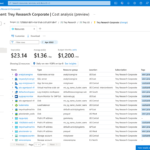
Azure Cost Management and Billing updates – April 2022
Whether you're a new student, a thriving startup, or the largest enterprise, you have financial constraints, and you need to know what you're spending, where, and how to plan for the future. Nobody wants a surprise when it comes to the bill, and this is where Azure Cost Management and Billing comes in. We're always […]